Understanding the Importance of CASBs in Cloud Security Strategies
Written on
Chapter 1: Introduction to Cloud Security Tooling
Welcome to the second installment of our Cloud Security Tooling series. In our previous discussion, we examined Cloud Security Posture Management (CSPM) and its implementation best practices in cloud settings. This article will focus on the role of Cloud Access Security Brokers (CASBs) and their significance in modern cybersecurity frameworks.

The most common cause of cloud data breaches stems from misconfigurations, underscoring the necessity of CSPMs. However, the second major threat to cloud security is data leakage. The convenience of sharing information in the cloud can inadvertently lead to significant data exposure.
Section 1.1: The Challenge of Data Leakage
Data is often dispersed across various platforms, including cloud providers and SaaS applications like OneDrive, Microsoft 365, and Salesforce, complicating user activity monitoring. Additionally, the prevalence of "Shadow IT" allows users to bypass established IT policies, leading to unauthorized cloud service usage without security teams' awareness. This situation poses a substantial challenge for cybersecurity professionals, who must manage the risks associated with data movement without imposing overly stringent controls.
Subsection 1.1.1: The Role of CASBs
A Cloud Access Security Broker (CASB) acts as a centralized control point for cloud applications, enforcing data protection policies and monitoring user behavior to uphold security standards. By positioning itself between users and cloud applications, a CASB can detect and alert on violations, such as unauthorized access or data transfers.
This video, titled "Cloud Security Tools 2022 | CSPM, CASB, CWPP Explained," provides a comprehensive overview of various cloud security tools, including CASBs, detailing their functionalities and importance in cloud environments.
Section 1.2: Key Features of CASBs
CASBs offer several essential features, including:
- Management of Shadow IT: CASBs can operate in proxy mode, enabling them to inspect data traffic between users and their browsers, immediately alerting or blocking the use of unauthorized cloud applications.
- Mitigation of Data Leakage: By utilizing proxy mode, CASBs can restrict sensitive data uploads and downloads, alerting administrators if personally identifiable information (PII) is uploaded to cloud storage.
- Integration with On-Premises DLP: CASBs can serve as extensions of existing on-premises Data Loss Prevention (DLP) systems, applying consistent policies across all environments.
- User Behavior Monitoring: CASBs provide insights into user activity, using contextual information (location, time, risk score) to enforce additional authentication when behaviors deviate from established norms.
- Zero Trust Enforcement: By scrutinizing and authenticating every user request, CASBs help implement a Zero Trust security model.
- Prevention of Cloud Malware Attacks: CASBs can scan files in real time, preventing malware from infiltrating cloud storage and conducting regular post-upload scans to combat ransomware threats.
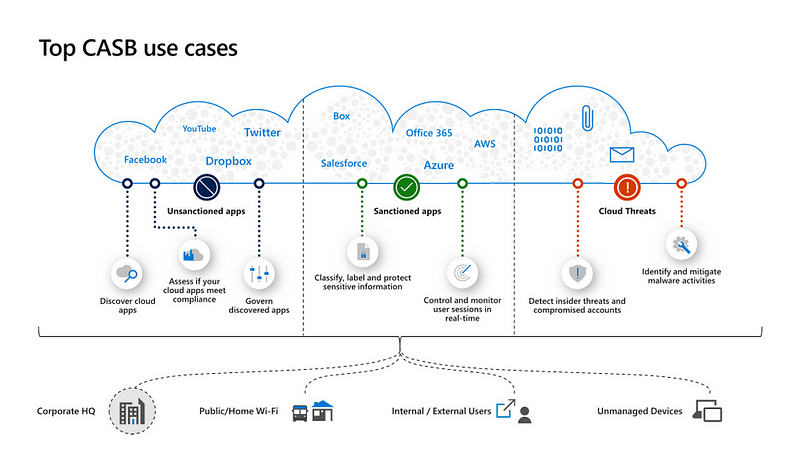
Source: Microsoft
If you're curious about how CASBs differ from CSPMs, the distinction is straightforward: CSPMs assess the security posture of your cloud environment, while CASBs focus on the security status of your cloud users.
Chapter 2: Understanding CASB Operation Modes
CASB solutions typically operate as cloud services (although some can be on-premises) and function in three primary modes: reverse proxy, forward proxy, and API mode.
The video "Overview: Microsoft Cloud App Security (CASB)" provides a detailed explanation of how CASBs operate, including the various modes and their respective advantages.
Section 2.1: Reverse Proxy Mode
In reverse proxy mode, CASBs intercept all user requests, allowing them to enforce DLP policies in real time and prevent malicious activities.
Section 2.2: Forward Proxy Mode
Forward proxy mode necessitates the installation of an agent on users' devices to forward traffic to the CASB. While this method is generally faster, it requires additional setup.
Section 2.3: API Mode
API mode is the simplest to implement, connecting directly to cloud applications for monitoring. Although effective for identifying policy violations, it lacks the real-time enforcement capabilities of reverse proxies.
Key Considerations When Implementing a CASB
If you're considering a CASB solution, keep these points in mind:
- Ensure compatibility with your cloud environment, as not all CASBs support every application.
- Implement both reverse proxy and API modes for comprehensive coverage; relying on one alone may leave gaps.
- Verify that Single Sign-On (SSO) is available, as many CASBs require it for reverse proxy functionality.
- Thoroughly test policies before deploying reverse proxy mode to avoid blocking legitimate user activities.
Best of luck on your CASB implementation journey!

Taimur Ijlal is a recognized leader in information security with over 20 years of experience in cyber-security and IT risk management within the fintech sector. Connect with Taimur on LinkedIn or visit his blog for insights. He also runs a YouTube channel, "Cloud Security Guy," where he shares valuable information on cloud security, AI, and career guidance in cybersecurity.